Given that the trademark part of USPTO is aaqgs-criminally responsible to torturous behavior towards TBI-sick me, unrelieved as lacking in funds then and statuary time limitation now; it is terribly important to me to invent a scheme that makes at least that section irrelevant and then trash its employees of wasteful unnecessary people.
There is important cryptography insight, one internet insight and two physics insights that make this revenge possible. Given its scope, it will do banknotes, articles and what not – enough to emfubar the sub animals.
The cryptography insight is - there is NO solution to base ^ power % mod = value when all but power is known. It becomes even harder if mod is not known as well.
The internet insight is - it is possible to completely shield a computation in clouds, returning the answer within micro-seconds sand transparently increase the computers responsible for identical computations proportional to paying load.
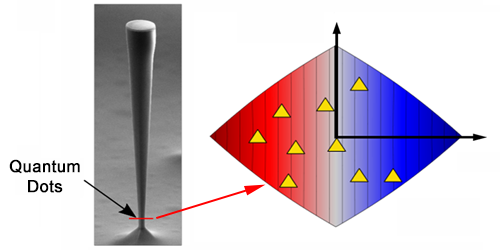
One physics insight is – quantum dots embedded in pillars by self-assembly process are quantum randomly placed.
Another physics insight is – under uniform strain, the dots photo-luminescence changes. A french group has already developed technology to determine the dot positions thus.
https://physics.aps.org/synopsis-for/10.1103/PhysRevLett.118.117401
Application:
Given the results, consider the deposit of such a substrate on any article. The dots vector forms a random large number from which an unknown subset is selected but the digital root of the selectin is recorded.
On the internet using clouds are sent the measurements and the digital root. A process remotely selects bits based on digital exponentiation to unknown power. Bits from measurements are subset based on this result, and the number is discret powered again to another unknown power (selected by the class of goods being protected). The result is sent back with ant-hack bits. After decode, it must be the same displayed on the article.
Why does it work?
- Even trillion-trillion collection of pairs of (number printed, result expected) can be used to decode values hidden
- Reuse of a valid number
pair elsewhere is prevented by requiring same quantum dot pair
elsewhere which is impossible due to uncontrolled quantum
randomizing!
No comments:
Post a Comment